At WWDC 2019, Apple unveiled a new ‘Find My’ app, which is basically a combination and replacement of Find My Friends and Find My iPhone. The app offers a very useful feature that let you find your lost devices even when they’re not connected to WiFi or a cellular network.
Talking about Mac, it also introduces a native ‘Find’ app for the first time as an alternative to iCloud on the web. ‘Find My’ app is available across iOS and Mac platforms and help you locate your lost iPhone, iPad or Mac in no time.
The new app uses nearby Bluetooth devices and enables your lost device to communicate with any nearby Apple device, sending its location right back to you.
Apple introduced the Find My app in the June 2019. According to WIRED, this technology is not at all a risk to your privacy, the company has designed Find My feature with privacy in mind.
This app works on a strong encryption system that doesn’t allow people to use it for tracking purposes. Your personal location will remain unavailable to every person aiming to intercept your device’s Bluetooth signal. Let’s have a look at how the system actually works step by step.
Also Read: Proxy vs VPN: The Real Difference
How Apple’s ‘Find My’ Offline Tracking Actually Works?
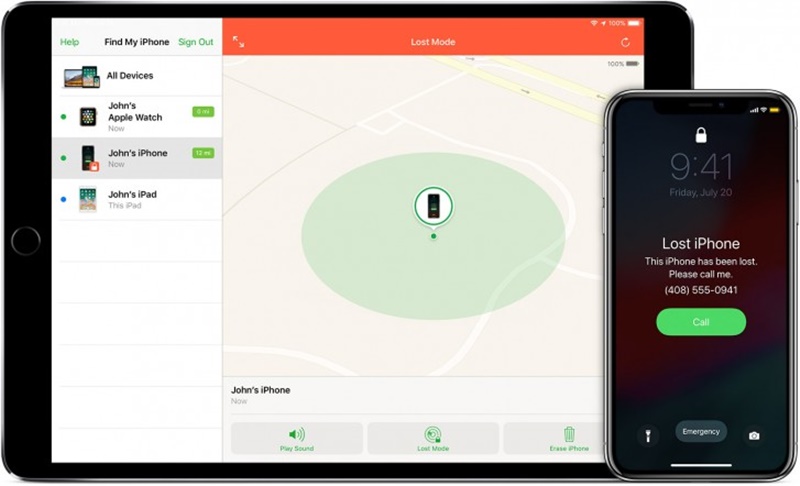
Step 1:
First of all, in order to use Find My app, you’ll need at least two Apple devices. It generates a unique private key and shares it on all those confirmed devices via end-to-end encrypted communication, and thus ensures only those machines possess the key.
Step 2:
Each device will also generate a public key that can be used to encrypt data, just like any other public key encryption setups.
This data can only be decrypted by the devices which have the corresponding secret decryption key. The public key is the ‘beacon’ that your devices will broadcast via Bluetooth to nearby devices.
Step 3:
As I already said, Apple has taken care of the security quite well. The public key frequently changes and rotating to a new number at regular interval of time.
Though Apple doesn’t reveal how often the key rotates, they confirmed it retains its ability to encrypt data that only your devices can decrypt.
Also, every time the key rotates, it makes much harder for anyone to misuse your Bluetooth beacons and track your movements.
Also Read: How to Run iOS Apps on Android Device?
Step 4:
Suppose, someone stole your iPhone and it’s now disconnected from the Internet. Your phone will keep emitting and rotating its public key via Bluetooth.
A nearby stranger’s iPhone will pick up the signal, check its own location, and encrypt that location data using the public key it picked up from the stolen iPhone.
The public key rotates frequently and doesn’t contain any personal information so that stranger’s iPhone can’t link to the lost device its prior locations.
Step 5:
Then, the stranger’s iPhone uploads two things to Apple’s server: First the encrypted location and secondly, a hash of the stolen iPhone’s public key, which will serve as an identifier. Here you should also remember, the secret key is even unknown to Apple, so they will not able to decrypt the location.
Step 6:
To find your stolen iPhone, turn to your second Apple device that contains both the private keys and has generated the same series of public keys. Tap a button to find your iPhone. Now, the second Apple device also uploads the same hash of the public key to Apple as an identifier.
The process ends when Apple search upon the millions of stored encrypted locations to find the matching hash.
Step 7:
Finally, the company returns the encrypted location of the stolen iPhone to your second Apple device, which will further use its private key to decrypt it and tell you the last known location of the phone.
As Apple has never seen the exact location and hashing functions are always irreversible, it can never misuse the hashed public keys to collect more information about you or your previous locations.
Though it might sound extremely complex, the company said that the system is subjected to change before it’s actually released in MacOS Catalina and stable version of iOS 13 later this year. The true security of the system will depend on the details of its implementation. If the company manages it will help millions of Apple users around the globe.












