On instant messaging apps like WhatsApp and Telegram, your messages and calls are usually secured with end-to-end encryption. But when it comes to sharing media files on these platforms, there’s every chance of a security flaw at work.
According to research by Symantec’s Modern OS Security team, hackers can use this security flaw to their own advantage. For example, hackers can exploit this flaw to tamper with your media files like personal photos and videos on WhatsApp.
What do your WhatsApp and Telegram media files have to do with this?
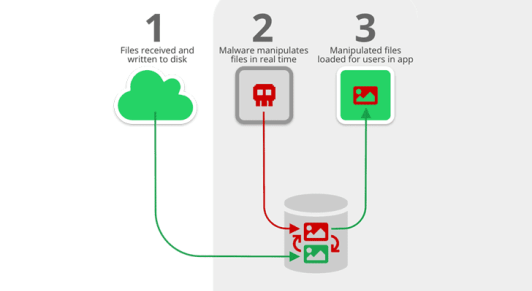
When you receive one or more media files through Telegram or WhatsApp on Android, these files are written to the disk. Next, the files are loaded in the respective apps’ chat user interface (UI) for users to go through.
Between these two actions, there’s a certain time lapse. This gap allows hackers to step into the scene and manipulate the media files without arousing the user’s suspicion. Once they’re done, these manipulated files are then loaded in the apps for the users to consume.
Android apps can store data and files either in internal or external storage locations. Files that are saved to internal storage can be accessed only by the app itself. But if the file is stored to an external storage public directory, then other apps or users can modify the file beyond the app’s control.
After you receive a media file on your device through WhatsApp, the app saves the file to external storage by default. This makes it easier for hackers to manipulate your media files by using the security flaw called ‘Media File Jacking’.
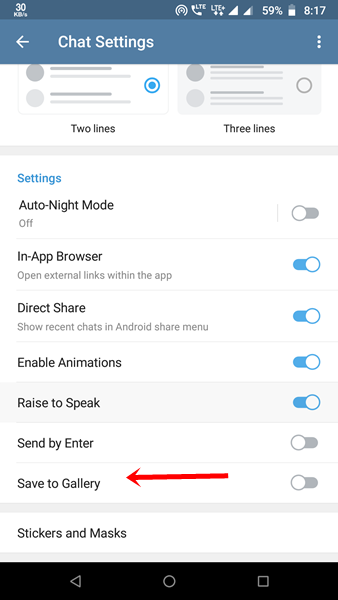
The flaw affects Telegram too, but only if you enable the ‘Save to Gallery’ feature on this IM app. Doing so will make Telegram store files in an external storage public directory, just like WhatsApp.
Also Read: How to Send WhatsApp Messages Without Saving the Contact on Your Phone
How can hackers exploit media file jacking?
https://youtu.be/bKBk6NBHw5s
A Media File Jacking attack can scam you into paying money to a hacker without your knowledge. For example, when you receive a PDF invoice file, a malicious app can detect it. Then, it can swap the displayed bank account information in the invoice with the hacker’s own. You won’t even know that it’s been changed.
Again, you may send your photo to one of your WhatsApp contacts, but what he/she will see is your face replaced with someone else’s.
How can you protect yourself?
You can protect yourself from Media File Jacking vulnerability on Telegram by turning off the ‘Save to Gallery’ feature in Chat Settings.
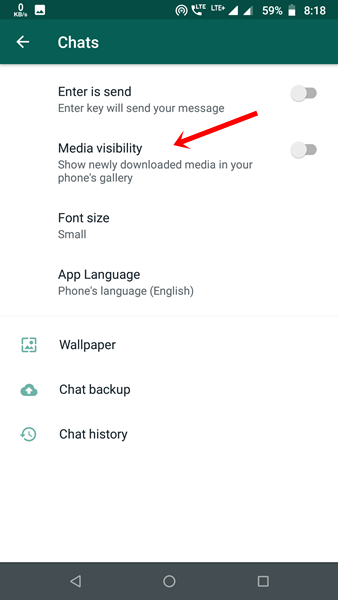
If you’re using WhatsApp, go to Settings > Chats and turn off ‘Media Visibility’.
Have you experienced a Media File Jacking attack? Let us know in the comments.