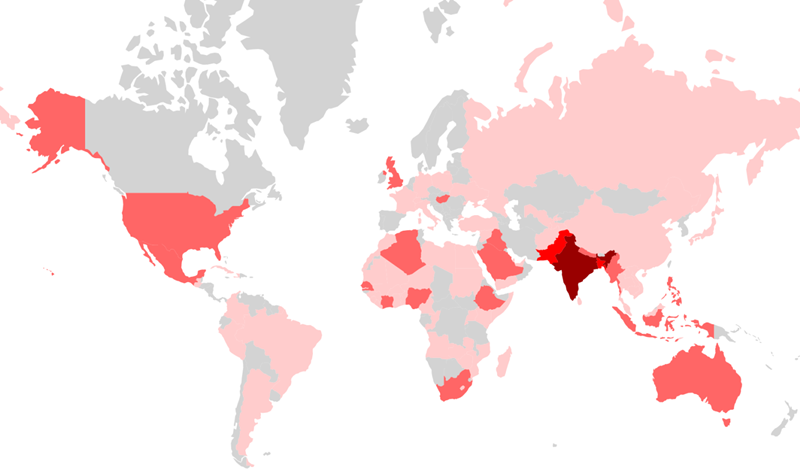
A new kind of mobile malware named ‘Agent Smith’ has recently infected about 25 million Android phones around the globe, displaying malicious ads without the user being aware of it. The malware, targeting installed apps like WhatsApp, has spread through 9Apps.com, a third-party app store owned by China’s Alibaba Group.
As India is WhatsApp’s biggest market, with almost 300 million users, around 15 million Indians have become the primary victims of this malware attack, although other Asian countries like Bangladesh, Pakistan, and Indonesia have also been hit. The U.K. and the U.S. have also reported more than 137,000 and 303,000 such attacks respectively.
Read: 10,000,000+ Users Have Downloaded This Fake Android App
According to CheckPoint, an Israeli security company, such hackers usually target more third-world countries, from where it’s easier to spread the malware to developed countries like Saudi Arabia, the U.S. and the U.K. This makes hackers’ attempts to infiltrate Google’s operating system even more successful.
How does Agent Smith work?
Typically, ‘Agent Smith’ completes its infection process in 3 phases: First, victims are lured to download ‘dropper’ apps related to games, photo utility, media player, or even adult entertainment from the app store.
Hackers use over 360 types of dropper apps on 9Apps.com for this initial step. Once a dropper app is downloaded and installed, it automatically decrypts itself and installs the core malware, which is disguised as a regular Google updating tool without an icon.
Next, the core malware accesses the Android phone’s installed app list, selects the apps on its list of victims, and then replaces the selected apps with malicious advertisements. Operating like a pay-per-click (PPC) system, the hackers make money with each click on a malicious advert.
The infected device brands include Xiaomi, Vivo, Oppo, and Lenovo, with Samsung at the top of the list. In fact, 26% of the ‘Agent Smith’ victims use Samsung, and devices with Android 5 and 6 have been affected the most, Check Point said.
Check Point warned that the malware infects the entire device repeatedly, coming back with new fraudulent ads every time. As per their estimates, 25 million Android phones being hit means that each victim must have been affected by 112 of such attacks on an average, leading to the overall number of infections totalling 2.8 billion.
Can Agent Smith hit Google directly?
The 5-member Check Point research team also discovered dormant versions of 11 apps on Google Play store, including Ludo Master, which were related to the ‘Agent Smith’ malware, indicating the hackers’ plan to target this app store next. So, the Google Play Store may be the next.
To prevent ‘Agent Smith’ from taking over your phone, go to your phone settings, and then the app list, and uninstall suspicious apps with names like Google Installer for U and Google Updater. Avoiding unofficial application stores might also help.












