For over two decades, VPNs have dominated the world of secure remote access. But now, as the number of remote users is growing fast and more applications are moving to the cloud, a VPN is likely to lose its footing.
VPNs are usually deployed to enable contractors and employees to access corporate networks. Sadly, VPNs operate on the all-or-nothing principle. When a VPN user is logged into a system, he or she gets broad access to the corporate network resources, which can expose sensitive information. In other words, a VPN does not provide adequate visibility and control threat inspections required for enterprise networks.
Also Read: Proxy vs VPN: The Real Difference
This unfortunate situation has seen many organizations develop an interest in software-defined perimeter (SDP), especially within the corporate circles. Gartner predicts that over 60% of enterprises will replace VPNs with SDP solutions by 2021. From a security perspective, the SDP technology has an advantage over the VPN.
However, we cannot rule out VPNs just yet. A recent research study conducted by the Cloud Security Alliance found out that more enterprises appreciate the value of SDP, but are still reluctant to leap.
So far, the main obstacle to adopting SDP has been finding a way to blend both technologies. In this article, we will explore the two technologies to help you understand which one is best for you. Let’s dive in.
Legacy VPNs Don’t Provide Adequate Capabilities
As mentioned earlier, VPNs have stood the test of time in securing corporate networks. However, VPNs operating by themselves do not provide optimum security. The safest security architecture is the one based on the principle of zero trust access. Here are some common VPN shortcomings.
1. Lack of Network Segmentation
A VPN is not equipped to grant access on a case-by-case basis. Typically, a conventional security setup requires you to connect a user to a network to access an app. So, to bring onboard users that are not on the same network, you will need to create a virtual network. This network will help you place these users on the same network as the app they want to access, which is likely to bring challenges.
To regulate remote access, enterprises have been relying on remote access solutions (RAS). However, from a security standpoint, this arrangement doesn’t guarantee zero-trust. That is why most organizations isolate different layers of security within their networks, blurring applications that are not intended to be seen.
Unfortunately, this blacklisted security approach can provide overly permissive access since security policies are often broad-level. Access policy models often grant users more access than what is needed. In other words, traditional VPNs are too lenient. They merely display broad configurations that may not have any meaning.
2. Unsuitable for Dynamic Networks
Most VPNs require constant management, tedious hardware, and usually don’t adjust to server changes. What it means is that VPNs make it hard to adjust for new network locations and additional users. Because of this, it is hard to manage cloud-based and hybrid computing models effectively.
3. Administration Hurdles
Sometimes, when organizations migrate to the cloud, they may encounter obstacles, while managing their VPN. In most cases, network administrators are expected to configure and coordinate firewall and VPN policies for all geographical locations. The extra configurations can make it harder for these administrators to control unauthorized access.
4. Changing Work and Networking Routines
Today, workers no longer use their desktops or laptops alone. They are likely to connect their mobile devices to the VPN as well, thus widening the perimeter and attack surfaces. As telecommuting becomes common, maintaining a well-defined perimeter is no longer possible.
The situation becomes even more complicated due to the use of increasingly sophisticated hacking techniques. Hackers have shown that they are ready to take advantage of gaps in the perimeter. So, organizations must look for something more robust.
Introducing the Software Defined Perimeter (SDP)
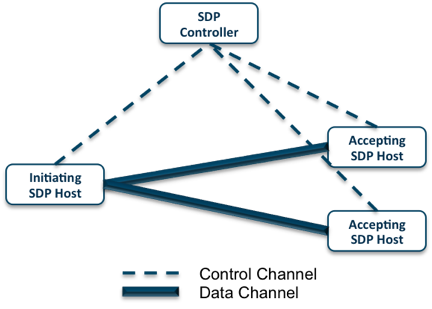
SDP is a zero-trust solution that employs two-key access criteria. Technically speaking, SDP solutions have several advantages over VPNs. With an SDP, security isn’t left to chance; there are no zones of trust. IT administrators have to define and grant access to each application.
Since users’ devices rely on point-to-point connections, the other network resources remain completely inaccessible. Some SDP packages allow for continuous verification of users, using an ID-based security technology.
Unlike VPNs, which need to be configured independently at each data centre or cloud, SDP allows IT administrators to run all their policies in the cloud. Since most of the things are managed in a centralized manner, a few resources are subjected to extra configurations when granting access to a virtual private cloud or a data centre.
Here are some of the benefits of using SDP:
- Global access – An SDP solution lets you deploy unified gateways, making it possible to access any resource from anywhere.
- Secured and encrypted – SDP solutions provide OS and application-level security, as well as the client and endpoint protection.
- Policies are user-centric – SDP systems allow enterprises to create access policies based on user attributes.
- Cost-effective – Automation minimizes the need for manual firewall updates.
Related One: 7 Things You Should Know to Prevent Online Shopping Frauds and Scam
Which Technology Is Best for You?
The software-defined perimeter is an emerging technology that is likely to improve cloud networking. This technology has provided a holistic solution to reduce the reliance on hardware across the entire security setup. It has simplified deployment, management, and visualization of network connections.
So, if you are migrating to the cloud, SDP might be the ideal security technology to deploy. It will enable you to implement a custom network access policy for resources and workers on an individual basis.
With that said, switching to SDP is not as easy as most people think. While there is a need for organizations to upgrade their approach to user access control, some existing security technologies don’t support SDP. Moreover, more organizations desire for a less costly and less disruptive deployment model. After all, VPNs have helped these organizations to secure their networks for close to three decades.
One of the main benefits of using a VPN is that it provides flexibility. Most VPNs connect multiple geographically distributed data centres, endpoints, and virtual private clouds with ease.
The bottom line is that legacy VPN technologies are no longer effective in preventing sophisticated cyber threats. Furthermore, the modern business environment has become more globalized, interconnected, and increasingly mobile. And this is where SDP comes in to address the security loopholes. You can make this technology even more effective by improving the performance of your devices.
Fortunately, there are several Mac and PC cleaning software that can help you with how to speed up your computer. Likewise, you can use reputable Android cleaners to optimize your smartphone or tablet for top performance.